CSE researchers win Best Paper Award at ACM MMSys 2024

CSE researchers have received Best Paper Award at the 2024 ACM Multimedia Systems Conference (MMSys) for their paper titled “OASIS: Collaborative Neural-Enhanced Mobile Video Streaming.” Authors on the papers include CSE PhD students Shuowei Jin, Ruiyang Zhu, and Xumiao Zhang; recent PhD alum Xiao Zhu; and Prof. Z. Morley Mao, as well as their collaborators at University of Minnesota (led by Prof Zhi-Li Zhang) and University of Southern California (led by Prof. Feng Qian).
MMSys is a top conference in multimedia systems, bringing together academic and industry researchers from around the world to share the latest findings in this area. The Best Paper Award, given to a select number of papers presented at the conference, seeks to recognize groundbreaking research that demonstrates exceptional ingenuity and importance.
Authors in CSE received the award in recognition of their development of OASIS, the first system for collaborative neural-enhanced video streaming that allows multiple users to stream high-quality videos in real time on their mobile devices.
Given the popularity of video streaming on platforms such as TikTok and YouTube, there is growing demand for higher-quality videos, particularly on mobile devices. However, limited network bandwidth can hamper the performance of mobile videos. Neural-enhanced streaming leverages neural networks to achieve super-resolution and enhance the quality of videos, but such methods require computational power far beyond that of the typical mobile device.
To alleviate this issue, CSE researchers have designed OASIS, a collaborative neural-enhanced video streaming framework that is able to leverage the computational capacity and network bandwidth of multiple mobile devices in order to improve the quality of video streaming.
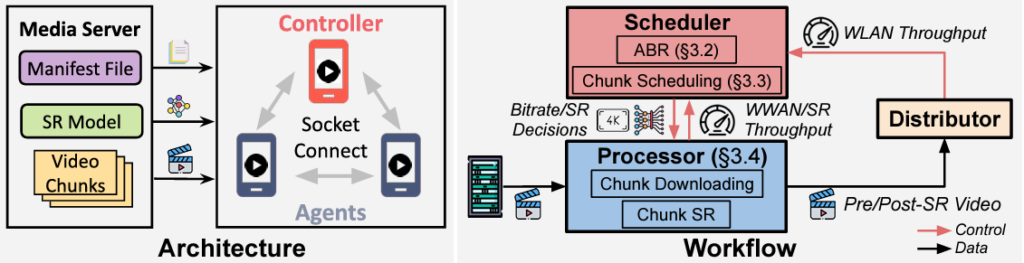
OASIS functions by aggregating a network of in-proximity mobile devices and separating video content into chunks. Chunks are forwarded to devices in the network, and a super-resolution algorithm is then run on each device to determine the optimal quality for these chunks, depending on the available computation power and bandwidth. Upsampled chunks are then shared across devices, allowing each user in the network to view high-quality video.
In experiments in networks of up to seven mobile devices, OASIS was found to significantly improve video streaming performance (by 35 to 230%) and reduce stall times (by 75 to 100%) relative to other systems. As more devices were added to the framework, OASIS also reduced energy consumption by up to 60%.
Through their research, the authors have shown OASIS to be an effective and efficient technique for improving video streaming performance on mobile devices.